This post introduces a simple infoleak in multiple browsers allowing attackers to track whether users have visited websites with a specific HTTP Strict Transport Security (HSTS) configuration. This bug affects a very small portion of websites, but happens to be useful for identifying TAILS users and determining precise versions of the Tor Browser Bundle. The most recent TAILS 1.2 release was the first to compile Tor Browser with ASLR enabled meaning that this simple infoleak could be used to hard code ROP chains for all prior TAILS releases.
| Tor Browser Status: | Test has not ran yet |
| Tor Browser ESR Version: | Test has not ran yet |
| TAILS Status: | Test has not ran yet |
| TAILS Version: | Test has not ran yet |
Abusing Strict Transport Security
HTTP Strict Transport Security is a web standard that specifies a protocol by which a web server can declare that browsers should only access it over TLS. This is accomplished either by presenting a Strict-Transport-Security HTTP header with a timeout, or by a look-up in an HSTS list distributed with the browser. The HSTS standard specifies that if a host is using HSTS then it should redirect HTTP port 80 requests to HTTPS over port 443; however, for all other ports (e.g. 8080) it should reconnect on the same port and use HTTPS.
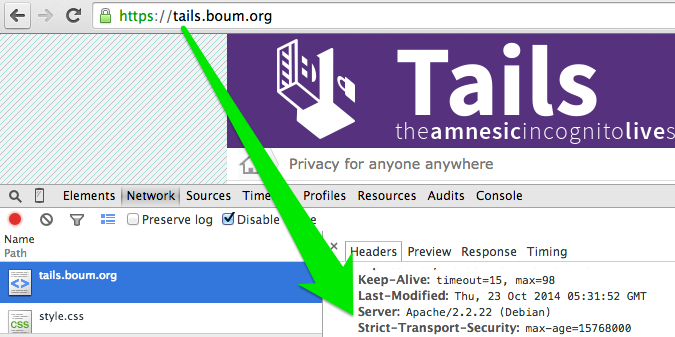
The implementation of this behavior in Firefox, Chrome, and Safari allows an attacker to track whether a user has visited a domain that implements HSTS by using the HSTS HTTP header instead of being listed in the browser’s HSTS list. This is possible by trying to access a valid HTTP resource over port 443. If the user has the website in their HSTS cache then the request will be transparently accessed over HTTPS and succeed; however, if the host is not in the cache it will try to use plaintext HTTP over port 443 and fail on most server configurations. This is interesting, but generally of limited use because most major HSTS-enabled websites come in the default browser lists so this test will fail; this only works against websites presenting the HSTS header without being present in the browser list.
Profiling the Tor Browser Bundle
The Tor Browser Bundle is based on Firefox Extended Support Release. Mozilla releases a new ESR major version once a year with periodic minor security updates afterwards. Aside from security patches, ESR releases also update the built-in HSTS lists. In order to avoid fingerprinting, ESR updates do not reveal the ESR minor version. Furthermore, Tor Browser Bundle also conceals the Operating System version by always reporting Windows NT 6.1. We can reasonably assume that traffic coming from a Tor exit node with an ESR release major version claiming that Operating System version is a Tor Browser Bundle user.
Because the HSTS list changes with almost every ESR release, we can determine the exact ESR version by performing the attack above. We can identify changes in the HSTS list between every minor release and determine which of those entries are present on the HSTS list.
Profiling TAILS
We can also use this infoleak to reliably profile TAILS users with almost no false-positives. The TAILS Tor Browser has it’s home page set to https://tails.boum.org, a domain that perfectly happens to use the Strict-Transport-Security header without being present in Firefox’s HSTS list. We can identify TAILS users by checking whether the user is using Tor Browser and checking whether the user has visited that domain. We can be reasonably assured that this is a TAILS user because Tor Browser doesn’t cache HSTS entries locally, meaning that the user must have specifically visited the TAILS domain in the same browsing session.
TAILS is released on the same schedule as Firefox ESR so using the Tor Browser profiling techniques above we can also tell exactly which version of TAILS someone is using by identifying their ESR version.
Adding the TAILS domain to the HSTS list would be sufficient to mitigate this specific issue; however, removing the homepage is preferable since the TAILS website has already been defaced once and serves as a watering hole for all TAILS users.
Update (12/9/14): You can follow along on Bugzilla bug 1090433, looks like Chrome merged a fix but then had to revert.